
Processing Strategic International Marketing Data
Verification of Business Contacts Information
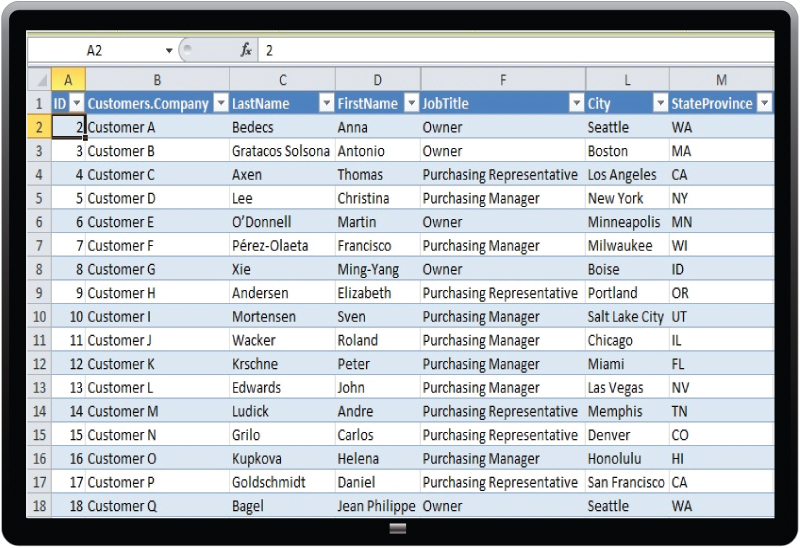
Appending and Verification of Company Data
Customers Relationship Management Strategy in the international market is a major factor of successful business operations. Improving your CRM data quality will increase productivity and sales rates.
VERIFY BUSINESS CONTACT INFORMATION
Marketing data quality worsen with time. REEID verifies contact information across a few most common languages. By verification process, we can proof whether the contact is still working at company and if so update their current position and provide their publicly available links.
Improved marketing data accuracy obviously will increase delivery rates and overall responses.
APPEND AND VERIFY COMPANY DATA
We will amend your CRM to be more complete for each company contact provided. We will source and enrich company information, including the headquarter address, website, phone number and published company description. Research is conducted on the Internet via publicly available trusted sites such as Linkedin or Facebook.
DATA SECURITY MEASURES
We prioritize the security of your data and our resources with exceptional diligence. Recognizing the need to protect certain documents and information from unprivileged individuals and automated systems, we have implemented rigorous safety controls and methodologies across our business units:
- We don’t use cloud based storage services (Google, Dropbox etc.) for sensitive data ( unless specified otherwise by Customer)
- We don’t use outsourced SMT (Statistical Machine Translation Engines) unless specified otherwise by Customer
- We don’t Build, Train, and Deploy Machine Learning systems and process datasets with use of cloud based third parties engines unless specified otherwise by Customer
- We are using only secured transmission protocols for external communication
- Strong files encryption within local storages and Distributed DMS
- Robust access privileges to our online platforms (profiles, roles, sharing rules)
- Access control on databases records level
- MFA authentication for all access to sensitive data
- Data destruction and disposal procedure in place
- Intrusion prevention system
- Multilayer data loss prevention (DLP) systems and procedures in place
- Data anonymization procedures (important while outsourcing projects)
- Regular Security & Confidentiality Audits
- Data Centers in Europe and Asia (depending on data security requirements, certain DC is selected)
- Full GDPR compliance
- Data protection compliance in line with regulations of the countries out of Euro-zone